Dallas Lock 8.0 Сервер Безопасности: сбор событий из СУБД MS SQL
Данное руководство описывает процесс настройки сбора и отправки событий Dallas Lock 8.0 Сервер Безопасности в R-Vision SIEM.
Предварительные требования
-
Сетевая доступность сервера СУБД источника по целевому порту и протоколу для каждой ноды кластера SIEM.
-
Учетная запись (далее — УЗ) в СУБД с правами на чтение таблиц, используемых Dallas Lock 8.0 Сервер Безопасности.
Настройка Dallas Lock 8.0 Сервер Безопасности
Для сбора событий Dallas Lock 8.0 Сервер Безопасности из базы данных MS SQL необходимо настроить подключение R-Vision SIEM под служебной УЗ с соответствующими правами.
Создание учетной записи в СУБД MS SQL
Чтобы создать сервисную УЗ, подключитесь к СУБД с правами администратора. Для этого выполните следующие действия:
-
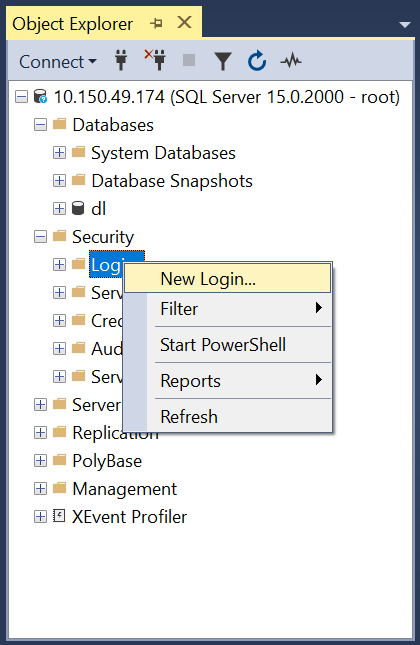
Войдите в веб-интерфейс SQL Server Management Studio.
-
Откройте контекстное меню Logins.
-
Выберите в контекстном меню вариант New Login.
-
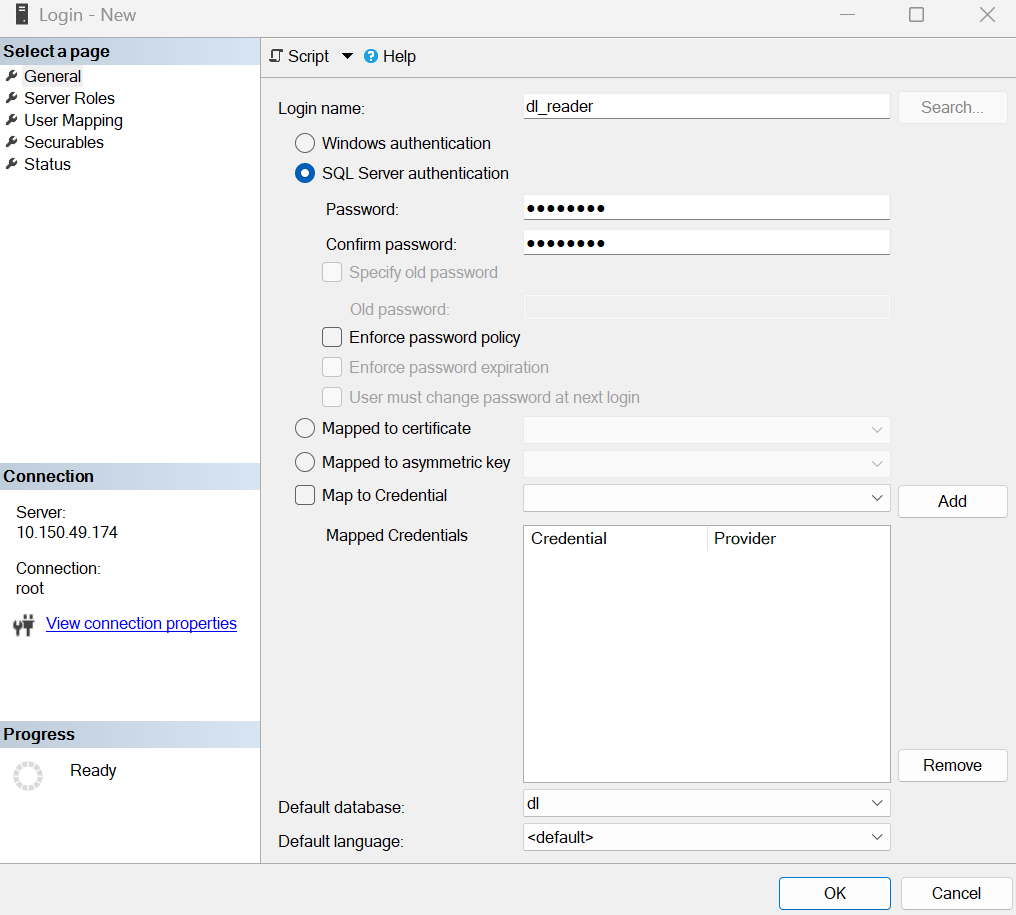
В появившемся окне создайте сервисную учетную запись.
-
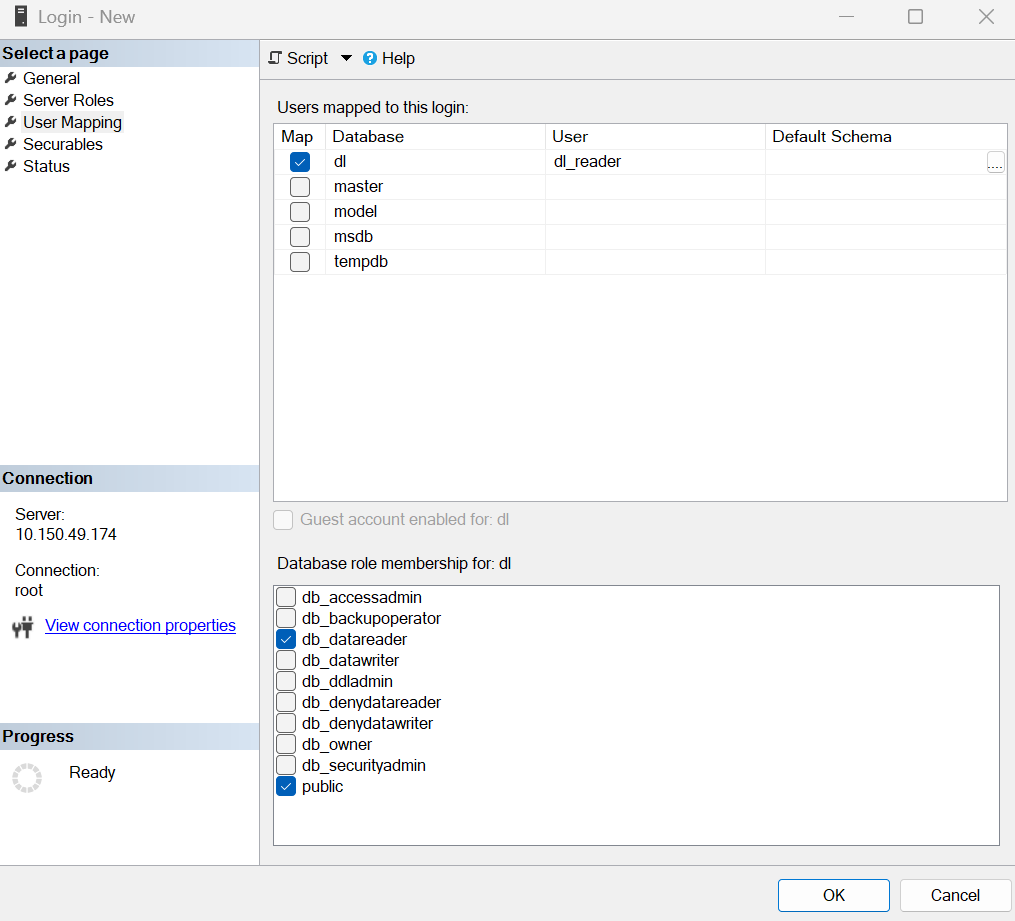
Предоставьте учетной записи права на чтение базы данных Dallas Lock.
-
Нажмите на кнопку OK.
Настройка сервера MS SQL
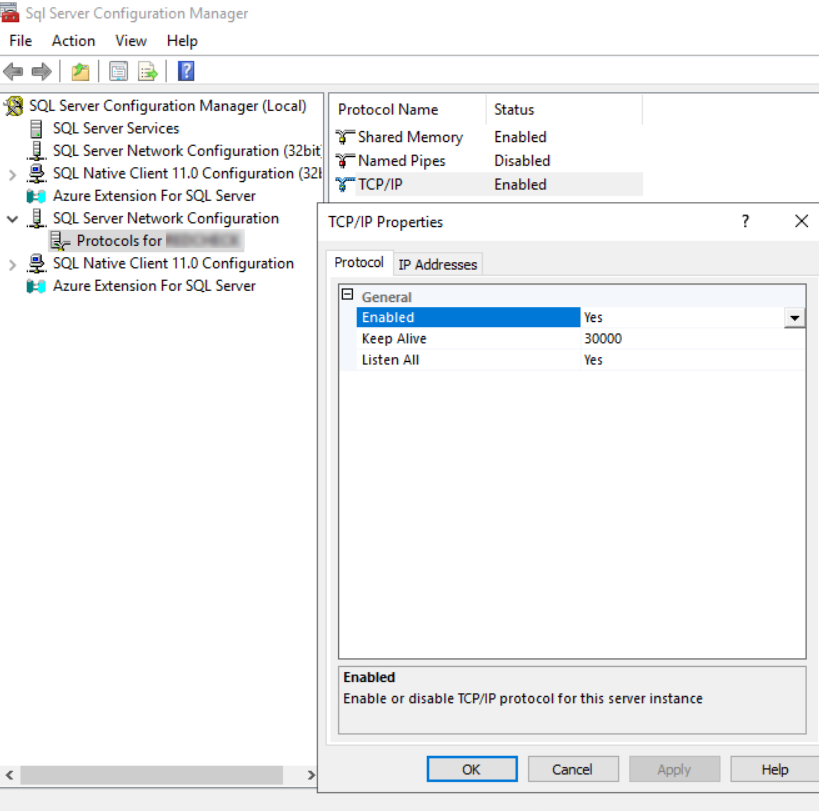
В настройках SQL Server Configuration Manager убедитесь, что протокол TCP/IP включен в конфигурации сети SQL Server.
Настройка журналирования Dallas Lock 8.0 Сервер Безопасности
Необходимо настроить периодичность сбора событий с конечных АРМ на Сервер Безопасности. Для этого выполните следующие шаги:
-
Откройте панель администратора Сервера Безопасности.
-
Нажмите на кнопку
 и в выпадающем меню выберите вариант Параметры сервера безопасности. Откроется окно настройки сервера безопасности.
и в выпадающем меню выберите вариант Параметры сервера безопасности. Откроется окно настройки сервера безопасности.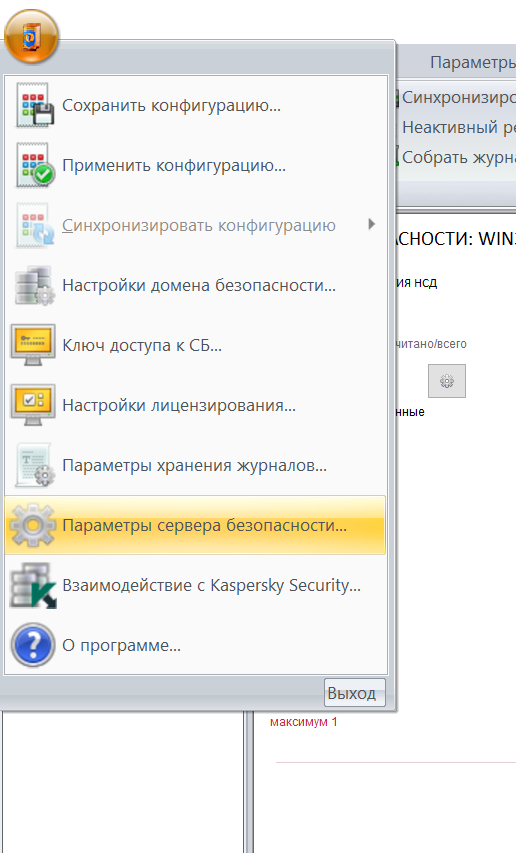
-
В появившемся окне на вкладках WINDOWS и LINUX установите для параметра Частота периодического сбора журналов минимально возможное значение
5 минут.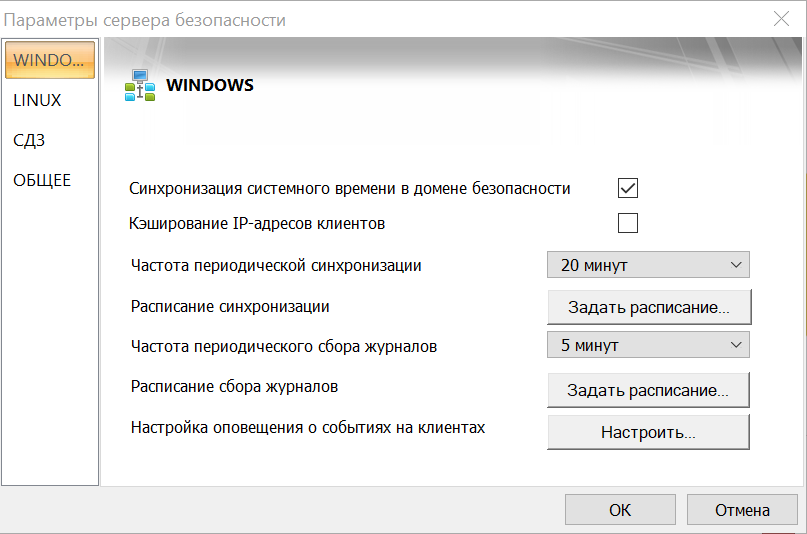
-
Нажмите на кнопку ОК.
Настройка на стороне Dallas Lock 8.0 Сервер Безопасности завершена.
Настройка в R-Vision SIEM
Для настройки сбора и нормализации событий источника в R-Vision SIEM выполните следующие шаги:
-
В интерфейсе R-Vision SIEM создайте секрет со строкой подключения. Для этого:
-
Перейдите в раздел Ресурсы → Секреты.
-
Нажмите на кнопку Создать (
).
-
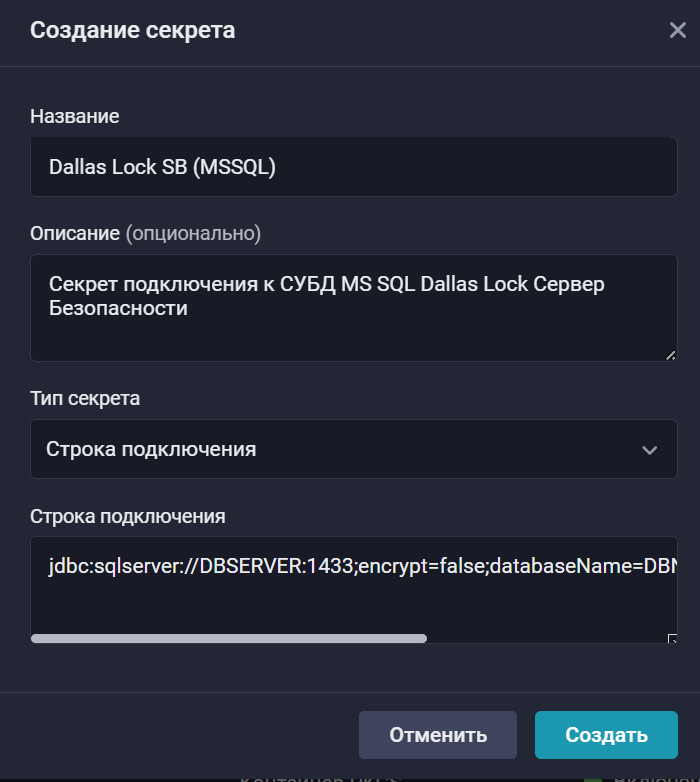
В раскрывшемся окне создания секрета заполните поля:
-
Название: введите название секрета.
-
Описание (опционально): опишите, для чего будет использоваться секрет.
-
Тип секрета: выберите вариант Строка подключения.
-
Строка подключения — введите строку вида:
jdbc:sqlserver://DBSERVER:1433;encrypt=false;databaseName=DBNAME;user=dl_reader;password=passw0rdЗдесь:
-
DBSERVER— FQDN или IP-адрес сервера СУБД. -
DBNAME— название экземпляра БД. -
1433— порт подключения.
-
-
-
Нажмите на кнопку Создать.
-
-
В интерфейсе R-Vision SIEM создайте новый конвейер в коллекторе.
-
Добавьте на конвейер элемент Точка входа со следующими параметрами:
-
Название: введите название точки входа.
-
Тип точки входа: выберите вариант Database.
-
Драйвер базы данных: выберите вариант MS SQL.
-
Адрес подключения: выберите секрет, созданный ранее.
-
SQL-запрос — введите запрос вида:
SQL-запрос
SELECT TOP 10000 'CONNECT' AS journal_name ,recID AS connect_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,processName AS process_name ,processID as process_id ,permit AS permit ,EventOnConnect AS event_on_connect ,DnsName AS dns_name ,protocol AS protocol ,localAddress AS local_address ,(LocalPort & 255) * 256 | cast((LocalPort/256) & 255 as bigint) AS local_port ,RemoteAddress AS remote_address ,(RemotePort & 255) * 256 | cast((RemotePort/256) & 255 as bigint) AS remote_port ,inDataLen AS in_bytes ,outDataLen AS out_bytes ,ruleId AS rule_id ,NULL AS alarm_level ,NULL AS rule_action ,AddressType AS address_type ,NULL AS src_address ,NULL AS dst_address ,NULL AS signature_number ,NULL AS signature_info ,NULL AS computer_name ,NULL AS comment ,NULL as parameter ,NULL as action ,NULL as type_of_attack ,NULL as target_user_name ,NULL AS latest_protocol_id ,NULL AS direction ,NULL AS bytes ,NULL AS resource ,NULL AS printer_name ,NULL AS document ,NULL AS printer_port ,NULL AS pages_printed ,NULL AS copies_printed ,NULL AS shadow_copy ,NULL AS wrong_user_pw ,NULL AS logon_mode FROM [dbo].[Connect] where dateAndTime >= DATEADD(MINUTE, -5, GetDate()) UNION ALL SELECT TOP 10000 'PACKETS' AS journal_name ,recID AS packets_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,processName AS process_name ,processID as process_id ,permit AS permit ,NULL AS event_on_connect ,DnsName AS dns_name ,NULL AS protocol ,localAddress AS local_address ,(LocalPort & 255) * 256 | cast((LocalPort/256) & 255 as bigint) AS local_port ,RemoteAddress AS remote_address ,(RemotePort & 255) * 256 | cast((RemotePort/256) & 255 as bigint) AS remote_port ,NULL AS in_bytes ,NULL AS out_bytes ,ruleId AS rule_id ,NULL AS alarm_level ,NULL AS rule_action ,AddressType AS address_type ,NULL AS src_address ,NULL AS dst_address ,NULL AS signature_number ,NULL AS signature_info ,NULL as computer_name ,NULL AS comment ,NULL as parameter ,NULL as action ,NULL as type_of_attack ,NULL as target_user_name ,LatestProtocolID AS latest_protocol_id ,direction AS direction ,length AS bytes ,NULL AS resource ,NULL AS printer_name ,NULL AS document ,NULL AS printer_port ,NULL AS pages_printed ,NULL AS copies_printed ,NULL AS shadow_copy ,NULL AS wrong_user_pw ,NULL AS logon_mode FROM [dbo].[Packets] where dateAndTime >= DATEADD(MINUTE, -5, GetDate()) UNION ALL SELECT TOP 10000 'IPS_TRAFFIC' AS journal_name ,recID AS traffic_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,processName AS process_name ,processID AS process_id ,NULL AS permit ,NULL AS event_on_connect ,NULL AS dns_name ,protocol AS protocol ,NULL AS local_address ,NULL AS local_port ,NULL AS remote_address ,NULL AS remote_port ,NULL AS in_bytes ,NULL AS out_bytes ,NULL AS rule_id ,AlarmLevel AS alarm_level ,ruleAction AS rule_action ,AddressType AS address_type ,SourceAddress AS src_address ,DestAddress AS dst_address ,SignatureNumber AS signature_number ,Info AS signature_info ,NULL AS computer_name ,comment AS comment ,NULL AS parameter ,NULL AS action ,NULL AS type_of_attack ,NULL as target_user_name ,NULL AS latest_protocol_id ,NULL AS direction ,NULL AS bytes ,NULL AS resource ,NULL AS printer_name ,NULL AS document ,NULL AS printer_port ,NULL AS pages_printed ,NULL AS copies_printed ,NULL AS shadow_copy ,NULL AS wrong_user_pw ,NULL AS logon_mode FROM [dbo].[IPS_Traffic] where dateAndTime >= DATEADD(MINUTE, -5, GetDate()) UNION ALL SELECT TOP 10000 'PROCESS' AS journal_name ,recID AS processes_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,processName AS process_name ,processID AS process_id ,NULL AS permit ,NULL AS event_on_connect ,NULL AS dns_name ,NULL AS protocol ,NULL AS local_address ,NULL AS local_port ,NULL AS remote_address ,NULL AS remote_port ,NULL AS in_bytes ,NULL AS out_bytes ,NULL AS rule_id ,NULL AS alarm_level ,NULL AS rule_action ,NULL AS address_type ,NULL AS src_address ,NULL AS dst_address ,NULL AS signature_number ,NULL AS signature_info ,NULL AS computer_name ,NULL AS comment ,NULL AS parameter ,action AS action ,NULL AS type_of_attack ,NULL as target_user_name ,NULL AS latest_protocol_id ,NULL AS direction ,NULL AS bytes ,NULL AS resource ,NULL AS printer_name ,NULL AS document ,NULL AS printer_port ,NULL AS pages_printed ,NULL AS copies_printed ,NULL AS shadow_copy ,NULL AS wrong_user_pw ,NULL AS logon_mode FROM [dbo].[Process] where dateAndTime >= DATEADD(MINUTE, -5, GetDate()) UNION ALL SELECT TOP 10000 'IPS_APP_CTRL' AS journal_name ,recID AS app_ctrl_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,processName AS process_name ,processID AS process_id ,permit AS permit ,NULL AS event_on_connect ,NULL AS dns_name ,NULL AS protocol ,NULL AS local_address ,NULL AS local_port ,NULL AS remote_address ,NULL AS remote_port ,NULL AS in_bytes ,NULL AS out_bytes ,NULL AS rule_id ,NULL AS alarm_level ,NULL AS rule_action ,NULL AS address_type ,NULL AS src_address ,NULL AS dst_address ,NULL AS signature_number ,NULL AS signature_info ,NULL AS computer_name ,comment AS comment ,NULL AS parameter ,NULL AS action ,TypeOfAttack AS type_of_attack ,NULL as target_user_name ,NULL AS latest_protocol_id ,NULL AS direction ,NULL AS bytes ,NULL AS resource ,NULL AS printer_name ,NULL AS document ,NULL AS printer_port ,NULL AS pages_printed ,NULL AS copies_printed ,NULL AS shadow_copy ,NULL AS wrong_user_pw ,NULL AS logon_mode FROM [dbo].[IPS_App_Ctrl] where dateAndTime >= DATEADD(MINUTE, -5, GetDate()) UNION ALL SELECT TOP 10000 'ACCOUNT' AS journal_id ,recID AS accounts_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,NULL AS process_name ,NULL AS process_id ,NULL AS permit ,NULL AS event_on_connect ,NULL AS dns_name ,NULL AS protocol ,NULL AS local_address ,NULL AS local_port ,NULL AS remote_address ,NULL AS remote_port ,NULL AS in_bytes ,NULL AS out_bytes ,NULL AS rule_id ,NULL AS alarm_level ,NULL AS rule_action ,NULL AS address_type ,NULL AS src_address ,NULL AS dst_address ,NULL AS signature_number ,NULL AS signature_info ,computerName AS computer_name ,comment AS comment ,NULL AS parameter ,action AS action ,NULL AS type_of_attack ,targetUserName as target_user_name ,NULL AS latest_protocol_id ,NULL AS direction ,NULL AS bytes ,NULL AS resource ,NULL AS printer_name ,NULL AS document ,NULL AS printer_port ,NULL AS pages_printed ,NULL AS copies_printed ,NULL AS shadow_copy ,NULL AS wrong_user_pw ,NULL AS logon_mode FROM [dbo].[Account] where dateAndTime >= DATEADD(MINUTE, -5, GetDate()) UNION ALL SELECT TOP 10000 'POLICY' AS journal_name ,recID AS policies_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,NULL AS process_name ,NULL AS process_id ,NULL AS permit ,NULL AS event_on_connect ,NULL AS dns_name ,NULL AS protocol ,NULL AS local_address ,NULL AS local_port ,NULL AS remote_address ,NULL AS remote_port ,NULL AS in_bytes ,NULL AS out_bytes ,NULL AS rule_id ,NULL AS alarm_level ,NULL AS rule_action ,NULL AS address_type ,NULL AS src_address ,NULL AS dst_address ,NULL AS signature_number ,NULL AS signature_info ,computerName AS computer_name ,comment AS comment ,parameter AS parameter ,action AS action ,NULL AS type_of_attack ,NULL as target_user_name ,NULL AS latest_protocol_id ,NULL AS direction ,NULL AS bytes ,NULL AS resource ,NULL AS printer_name ,NULL AS document ,NULL AS printer_port ,NULL AS pages_printed ,NULL AS copies_printed ,NULL AS shadow_copy ,NULL AS wrong_user_pw ,NULL AS logon_mode FROM [dbo].[Policy] where dateAndTime >= DATEADD(MINUTE, -5, GetDate()) UNION ALL SELECT TOP 10000 'ACCESS' AS journal_name ,recID AS access_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,processName AS process_name ,NULL AS process_id ,NULL AS permit ,NULL AS event_on_connect ,NULL AS dns_name ,NULL AS protocol ,NULL AS local_address ,NULL AS local_port ,NULL AS remote_address ,NULL AS remote_port ,NULL AS in_bytes ,NULL AS out_bytes ,NULL AS rule_id ,NULL AS alarm_level ,NULL AS rule_action ,NULL AS address_type ,NULL AS src_address ,NULL AS dst_address ,NULL AS signature_number ,NULL AS signature_info ,computerName AS computer_name ,NULL AS comment ,NULL AS parameter ,action AS action ,NULL AS type_of_attack ,NULL as target_user_name ,NULL AS latest_protocol_id ,NULL AS direction ,NULL AS bytes ,resource AS resource ,NULL AS printer_name ,NULL AS document ,NULL AS printer_port ,NULL AS pages_printed ,NULL AS copies_printed ,shadowCopy AS shadow_copy ,NULL AS wrong_user_pw ,NULL AS logon_mode FROM [dbo].[Access] where dateAndTime >= DATEADD(MINUTE, -5, GetDate()) UNION ALL SELECT TOP 10000 'PRINT' AS journal_name ,recID AS print_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,processName AS process_name ,NULL AS process_id ,NULL AS permit ,NULL AS event_on_connect ,NULL AS dns_name ,NULL AS protocol ,NULL AS local_address ,NULL AS local_port ,NULL AS remote_address ,NULL AS remote_port ,NULL AS in_bytes ,NULL AS out_bytes ,NULL AS rule_id ,NULL AS alarm_level ,NULL AS rule_action ,NULL AS address_type ,NULL AS src_address ,NULL AS dst_address ,NULL AS signature_number ,NULL AS signature_info ,computerName AS computer_name ,NULL AS comment ,NULL AS parameter ,NULL AS action ,NULL AS type_of_attack ,NULL as target_user_name ,NULL AS latest_protocol_id ,NULL AS direction ,NULL AS bytes ,NULL AS resource ,printerName AS printer_name ,document AS document ,port AS printer_port ,pagesPrinted AS pages_printed ,copies AS copies_printed ,shadowCopy AS shadow_copy ,NULL AS wrong_user_pw ,NULL AS logon_mode FROM [dbo].[Printer] where dateAndTime >= DATEADD(MINUTE, -5, GetDate()) UNION ALL SELECT TOP 10000 'LOGON' AS journal_name ,recID AS logon_rec_id ,dateAndTime AS event_date ,clientName AS client_name ,mandatLevel AS mandat_level ,userName AS user_name ,result AS result ,NULL AS process_name ,NULL AS process_id ,NULL AS permit ,NULL AS event_on_connect ,NULL AS dns_name ,NULL AS protocol ,NULL AS local_address ,NULL AS local_port ,NULL AS remote_address ,NULL AS remote_port ,NULL AS in_bytes ,NULL AS out_bytes ,NULL AS rule_id ,NULL AS alarm_level ,NULL AS rule_action ,NULL AS address_type ,NULL AS src_address ,NULL AS dst_address ,NULL AS signature_number ,NULL AS signature_info ,computerName AS computer_name ,NULL AS comment ,NULL AS parameter ,NULL AS action ,NULL AS type_of_attack ,NULL as target_user_name ,NULL AS latest_protocol_id ,NULL AS direction ,NULL AS bytes ,NULL AS resource ,NULL AS printer_name ,NULL AS document ,NULL AS printer_port ,NULL AS pages_printed ,NULL AS copies_printed ,NULL AS shadow_copy ,wrongUserPW AS wrong_user_pw ,logonMode AS logon_mode FROM [dbo].[Logon] where dateAndTime >= DATEADD(MINUTE, -5, GetDate())В представленном запросе из каждой таблицы собирается по 10 000 событий. Если возникает проблема с выгрузкой событий, рекомендуется понизить количество событий, собираемых одним запросом. -
Поле идентификатора: заполнять не нужно.
-
Интервал запроса, секунд: введите значение
120.
-
-
Добавьте на конвейер элемент Нормализатор с правилом confident dallas_lock_SB (идентификатор правила: RV-N-134).
-
Соедините нормализатор с точкой входа.
-
Добавьте на конвейер элемент Конечная точка типа Хранилище событий.
-
Соедините конечную точку с нормализатором.
-
Сохраните и установите конфигурацию конвейера.
Пример конфигурации конвейера:
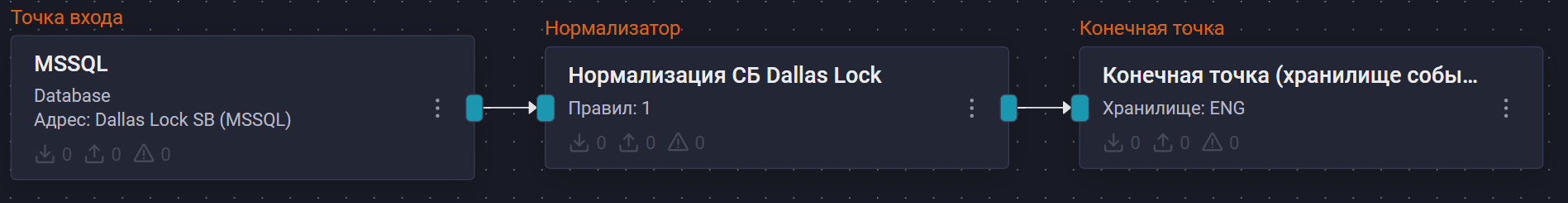
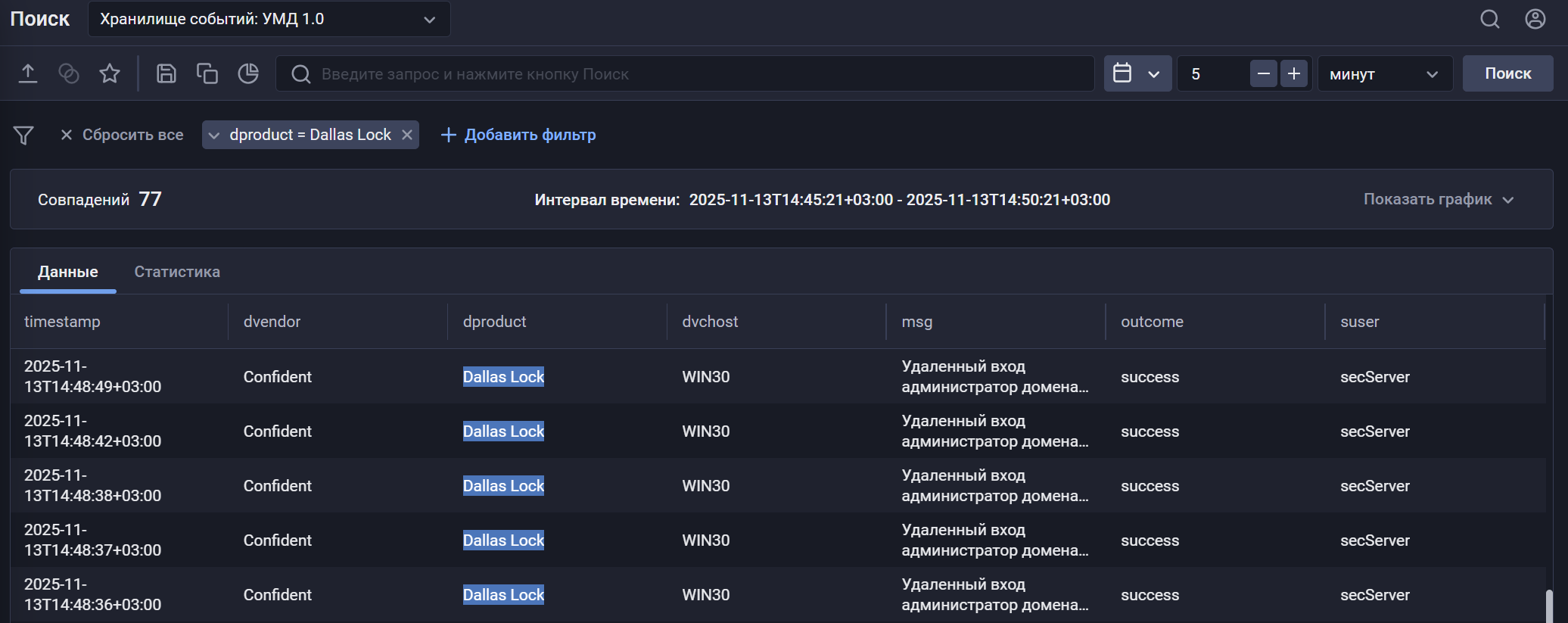
После настройки передачи событий, если настройка выполнена корректно, в хранилище начнут поступать события Dallas Lock 8.0 Сервер Безопасности.
|
Найти события Dallas Lock 8.0 Сервер Безопасности в хранилище можно по следующему фильтру:
|
Таблица маппинга
Таблица соответствия полей события для всех рассмотренных типов событий представлена по ссылке.
Была ли полезна эта страница?